
Combatting challenges for seasonal businesses is often met by hiring a temporary workforce. While these temporary employees play a critical role in ensuring smooth operations during peak periods, they also introduce unique challenges, particularly...
Physical and digital security risks are growing at a rapid rate, and leaving your security strategy on the back burner is no longer a viable option. Reactive measures, like waiting until after a security event occurs to determine next steps, are...

Safeguarding your assets, data, and personnel requires more than just a locked door. This means implementing a multi-layered approach that includes deterrence, detection, delaying, and response. Together, these four layers create a strong defense...
.jpg)
For any multi-location business, maintaining security and operational efficiency across numerous sites is a monumental task. A fundamental pillar of this security is robust key control. When managed poorly, the physical keys that grant access to...

Every single second counts during the chaotic moments of an emergency. Whether it's a fire alarm blaring or the unsettling sound of a break-in, the swiftness and effectiveness of your response can be the difference between minimizing damage and...

When a business chooses an access control solution, the decision extends far beyond simply buying hardware. It’s an investment, and evaluating the return on investment (ROI) is critical for long-term operational success and security.
.jpg)
Managing physical security across multiple business locations can quickly become a logistical nightmare. Spreadsheets, disparate databases, and manual processes often lead to confusion, inefficiencies, and significant security vulnerabilities....

While you’ve made a smart investment in commercial rekeyable locks, specifically those with interchangeable cores, your security system isn't a set-it-and-forget-it solution. Just like any other critical piece of equipment, your rekeyable locks...

Managers can find it daunting to ensure seamless operations while maintaining security in a bustling grocery environment. Managing access control is a critical yet often cumbersome responsibility. Traditional key systems, with their propensity for...

Your commercial lock system is more than just the cylinder where you insert your key. It's a comprehensive network of components working in tandem to provide robust security. Ancillary lock hardware plays a crucial supporting role in security...

According to Capital One Shopping Research, stores lost $121.6 billion to retail theft in 2023, and projections indicate shoplifting could cost retailers more than $150 billion in 2026. Internal theft is equally daunting. According to the National...

The humble lock cylinder is the core of your access control, determining who can enter your facilities and when. Although this pivotal player is often overlooked, understanding the different types of lock cylinders is crucial for safeguarding your...

From the busy aisles, the pharmacy, cash office and overlooked back rooms, a grocery store is a complex ecosystem with numerous areas requiring carefully managed access. This is where rekeyable locks emerge as a flexible and cost-effective solution,...
The Massachusetts cannabis market has experienced significant growth since the legalization of medical marijuana in 2012 and adult-use cannabis in 2016. As the market matures and new regulations for cannabis lounges begin to take shape, operators...

Security is a top priority for new cannabis operators, but with so many decisions to make before opening, it’s easy to feel overwhelmed. Between hiring security guards, installing cameras, and ensuring compliance, key control often gets...

Commercial locks are the silent guardians of your business. Protecting everything from valuable inventory (including the human ones) to confidential documents. Like any mechanical system—locks wear down over time, leading to potential security...

As a new cannabis licensee, securing your facility and protecting your employees should be a priority from day one. Even after obtaining your license, passing state and regulatory inspections hinges on your ability to maintain a secure and compliant...

In the last 5 years, retailers have experienced a staggering 93% surge in shoplifting incidents per year—along with a 90% spike in losses, according to the National Retail Federation’s 2023 Impact of Retail Theft Survey. As theft continues to rise,...

InstaKey Security Systems exhibited for the first time at the 13th annual MJBizCon in Las Vegas, held from December 4-6, 2024. From showcasing our innovative security solutions on the trade show floor to sponsoring the highly anticipated James Bong:...


Maintaining much-needed access with must-have security remains a delicate balance for franchise owners. Whether for one location or many, key control systems allow franchise owners to customize access from top-level managers to department heads to...
.jpg)
Maintaining robust security is crucial for retailers but often comes with a hefty price tag. Traditional security measures, such as standard key and lock systems, involve high initial costs and incur ongoing expenses for maintenance, rekeying, and...

As a business owner or manager, you need to be picky about which employees get keys for the business. One option you might consider is implementing interchangeable key core systems, making it easier to replace the lock if a key-holding employee...

The Oregon cannabis market is one of the oldest in the United States, with medical marijuana legalized in 1998 and adult-use cannabis legalization following in 2014. As this market has matured, Oregon has seen the evolution of cannabis security from...

A key tracking system provides the first line of defense when it comes to securing your business. When integrated into a key management system, it protects your staff and facilities and your bottom line. To ensure you have the right key tracking...

When it comes to securing a large commercial facility the lock system is a vital line of defense - and the costs of maintaining that security can really add up. One of the most fundamental security measures is the lock system itself. Traditional...

As parents, we all want to feel confident that our kids are safe and secure when they're at school. But in today's world, ensuring campus safety is an immense challenge that administrators must take extremely seriously. Schools have to be proactive...

Key management plays a pivotal role in security infrastructure, controlling access and safeguarding assets across a multitude of settings—from corporate offices to residential buildings. At the heart of modern key management solutions are...

Managing a restaurant is no small feat. Beyond the day-to-day operations of serving customers and maintaining quality, there lies the critical, yet often overlooked, aspect of key management. Traditional key management methods can be cumbersome and...

The importance of a robust and reliable commercial security locking system can't be overstated. Protecting your organization's assets, be it physicalor intellectual, is paramount. The question is, how can you be certain that your existing lock and...

Franchise owners often face unique challenges in maintaining security across multiple locations. A grand master key system simplifies key management while bolstering security and efficiency. This blog explores the advantages of implementing such a...

As a franchise owner, keeping a tight grip on operating costs is essential for maintaining profitability. While many cost-cutting strategies can impact your customers or staff, there is one often overlooked area that can yield significant savings -...

Decisions surrounding your company's key management system can have a surprising and significant impact on your Environmental, Social, and Governance (ESG) initiatives. By optimizing key management processes, companies can contribute to...

Security and accountability have never been more critical for organizations than they are today. Effective management of your company's key security system is critical. It is essential to have a robust system in place that not only ensures the...
It may seem obvious that commercial facilityshould track their company keys. After all, what self-respecting company would just hand company keys out to employees without a way to ensure security? The management of company keys is especially...

Ensuring robust security while managing costs effectively is crucial in the retail sector. For store managers and regional managers, the goal is to find solutions that are secure, cost-effective, and straightforward to manage. Enter rekeyable...

When it comes to the physical key security of your company, managing a key checkout system often emerges as a critical concern. On the surface, it seems simple enough: Keys are secured in a restricted space under the supervision of authorized staff.

As the holiday season rolls around, retail stores are not just bursting with shoppers but also with a heightened need for security. Amidst the festive cheer, ensuring the safety of employees and the store's treasures becomes paramount. Selecting a...
Whether your job is to track a few or a few thousand employees and an equal number of keys it can be an overwhelming task. If you’re using excel spreadsheets or a log book to keep track of who has what keys, you know it takes a significant amount of...

Security of fuel dispensers is becoming more and more critical to protect. Credit card skimming is on the rise all over the country because criminals realize how easy it is to install credit card skimming devices, leaving your station and your...

In the retail industry, even with wage increases, high rates of employee quitting persist. To address this concerning trend, employers must prioritize the things workers value most. By implementing strategic programs and initiatives, retail stores...

We are living in an era where the economic landscape is fraught with challenges. Inflation is hitting peak levels, causing the expenses associated with running a business to spiral upward. This reality hits especially hard in the grocery sector, an...

As a retail organization, your employees and customers are your most important asset. In the fast-paced world of retail, ensuring the safety and security of employees is paramount. With numerous customers, high-value merchandise, and various...

In the digital age, data centers are the beating hearts of global commerce and information exchange. These networked computer servers are the nerve centers where businesses or organizations store, process, and distribute massive volumes of data....

Employee turnover in the retail industry is a prevalent challenge that comes with significant costs. The retail industry faces considerable turnover rates, as highlighted in McKinsey's report on attracting and retaining frontline talent amid the...

One of the top concerns of any organization is security. Protecting your people, financial assets, inventory, and proprietary information, as well as regulating who has access, is a number one priority. Having a robust key management system is part...

In November of 2022, a pair of thieves stole $20,000 worth of diesel from a Hendersonville, Tennessee gas station. And they did it in a matter of hours in broad daylight. Could your fuel station afford to lose $20,000 in a single day from fuel theft?

If you work in a corporate or retail setting, you may have heard of master key systems. But do you know how they work and how to use them effectively? In this article, we’ll explore the basics of how a master key works and best practices for...

One of the essential tasks every facilities manager or loss prevention manager needs to consider is key control policy development. A proper key control policy helps to safeguard your organization, building, and employees by ensuring only authorized...

Physical security for a store’s loss prevention can take many forms. Whether you want to secure your inventory, guard your company's proprietary information, or keep your employees safe, you're most likely using a physical lock and key. Traditional...

When it comes to evaluating your lock and key program, security, and efficiency are your number one priority. One crucial aspect of security is key control, ensuring that keys are properly tracked and accounted for at all times. However, manually...

Every organization wants to maintain the security of their employees, goods, and facilities. Despite advancements in digital technology, there’s no more effective way to keep your company physically secure than with locks and keys. It can also be...

Every facility utilizes some level of key control to keep employees, assets, and facilities secure. Choosing a key control solution for your environment is only the first step. What happens after that determines how effective and costly your program...

There's no denying that mass shootings in businesses and public buildings have been on the rise in recent years, with some experts saying stores and malls are among the most at-risk locations. Many organizations are looking to build safe rooms in...

When a key goes missing at your multi-site organization, locks shouldbe changed as soon as possible. Your personnel and asset security could beat risk, and every second counts. Depending on your locks, you may need torekey or perform an...

The lock and key may seem like a simple mechanism. But recent technological advances have brought physical keyed security far ahead of its historical origins. In this article, we will take a look back at the early beginnings of the lock and key, and...

In the past, we’ve discussed the differences between traditional locks and interchangeable (IC) core locks in terms of security. But with consumers gravitating toward sustainability more and more these days, we can’t ignore the environmental impact...

There are many benefits to key control systems that include master keys. Particularly for multi-site organizations, master key systems are an important security tool that give your facilities managers necessary access to all areas of their location....

For as long as people have wanted to keep valuables safe, there have been locks and keys. While the shape, size, and security of locks have changed over time, their basic function is still the same: Needing a key to open a lock. Or at least, that's...

The only thing standing between your organization's assets and a security breach is the strength of your lock and key program and the accuracy of your security system records. Cloud-based key control makes it easier to keep your security records...

Even the best lock and key program needs to be evaluated periodically. You may think your facility is secure, but how do you know for sure? You may think it’s the most cost-effective program you can get, but your total operating expenses might be...
After you've established your physical security and your master key system, you need a way to track your master keys, locks, and user keys. It's the last step in maintaining key control. Poor key tracking will cost you in the long run. In this...
![Key Control: The Role of a Master Key [+Best Practice Tips]](https://info.instakey.com/hubfs/Key%20Control-%20The%20Role%20of%20a%20Master%20Key.jpeg)
It used to be that building managers and security personnel had to carry around multiple sets of keys to open individual rooms. Those keys could easily get lost, stolen, or duplicated. And if the security of one section became compromised, that...

Here's an alarming statistic:A burglary takes place every 18 seconds in the United States. Which means that your organization needs to make security a priority to ensure the safety of your employees, facilities, and products.

One of the biggest differences between a lock with a standard interchangeable core and one with an InstaKey rekeyable core is how they are rekeyed. Standard interchangeable cores need to be completely replaced with new cores for a rekey. That can...

There’s an area of keyed security that hasn’t been talked about much in the industry. That area is the protection of your organization’s most important asset. Locks aren't just for protecting inventory and equipment. They're for protecting people....

The closest a multi-site key control program can get to being perfect is on the first day it’s implemented. Over time, things can slip through the cracks and lead to a potential security compromise. Somebody may forget to keep key tracking data up...

When a facility key falls into the wrong hands, it puts the business, and everyone employed there at risk. The days of assigning keys to staff and hoping they don't make unauthorized duplicates are a thing of the past - at least they should be. If...

When looking at your total operating costs, it can be tempting to see your key control program as a line item you can cut back on. After all, your facility has locks, employees have keys, and you can trust your staff to be responsible. But mistakes...
You need a comprehensive key management system to control and monitor your organization's secure keyed access. The more keys and access points you have, the more complicated your key management becomes. While a simple spreadsheet might work just...
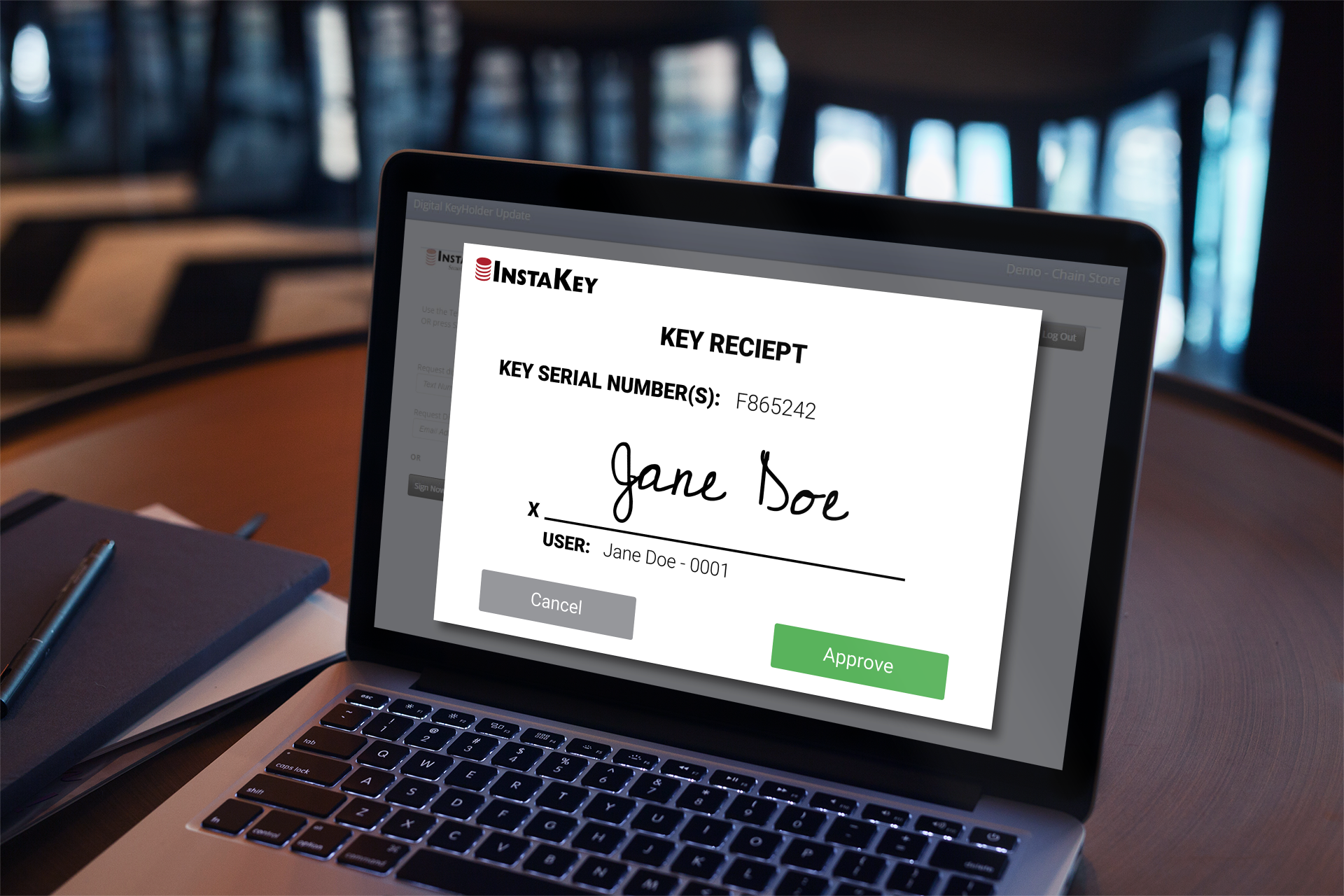
There are many ways digital key tracking software helps you keep track of keys, keyholders, doors, and locations easily and efficiently. Rather than wasting time with updating spreadsheets and calling a locksmith any time a key is lost or stolen,...



Changing the locks is an unavoidable part of running a business. Regardless of the size of your building, it’s always a nuisance, but it becomes more of a problem for multi-site organizations. Security breaches, staff turnover, and misplaced keys...




Loss prevention is an important part of maintaining physical security for retailers and other companies with a number of products, locations, and people to keep secure. Fortunately, improving physical security and loss prevention go hand in hand. By...

Recoring after a lost or stolen key is an expected part of most organizations' key control. It's a simple process that can save your business time and money. Interchangeable (IC) cores are commonly used in commercial and multi-site facilities...

Your site security is only as strong as your key control system. Business owners often have a false sense of security after installing an IC (Interchangeable Core) lock system throughout their organization. It's good to remember, an important part...
Key tracking is one of the foundational components of your larger key control system. Establishing good tracking practices can improve the day-to-day management of your mechanical keys, locks, and key holders, which contributes significantly to the...
.jpg)
For commercial organizations, there are countless components that make up a successful business and contribute to your bottom line. One of those components that can occasionally go unnoticed is physical security. In our modern age, many...

There are many aspects of our daily lives that we don’t often think about. Your locks and keys can be one of those. Locks are in use everywhere you go to reliably keep people, goods, and property safe. There is an entire industry that caters to...

As every large organization knows, the more facilities or stores you have to keep track of, the more complicated your facility management can become. This is particularly true for your security and loss prevention teams. Your bottom line can be...

For commercial organizations, the choices made to keep your products, people, and facilities safe can have a big impact on your bottom line. This is why physical security and key control, is so important for organizations of any size.

For retail organizations, maintaining the physical security of each retail location is vital to your loss prevention. But physical security can often be a balancing act between improving site security and maintaining cost efficiency. Determining...

Maintaining the physical security of your organization is a big job. Particularly if your company has many facilities, retail locations, or warehouses. Providing secure access and keeping track of who has what access gets more complicated the more...

Interchangeable cores, also known as IC cores, can simplify the security and key management processes of your business sites. The types of locks you use on doors in and out of your organization can play a big role in securing your employees,...
There are many components of creating key control for your organization that is streamlined and cost-effective. Your keyed security can have a big impact on the safety of your employees, facilities, and products. And not having a strong physical...

The success of your key management directly affects the security of your organization. While locks and keys are the first line of defense to protect your facilities, products, and employees, how well you manage your locks and keys can either...

Maintaining keyed security, particularly as a large, multi-site organization, involves keeping track of a lot of moving pieces. With many facilities, employees, products, and stakeholders, security is a complicated endeavor. While technology...

As every member of your loss prevention/asset protection team knows, maintaining your physical security can feel like an arcade game with pixelated threats popping up from behind every door. Unexpected events within your organization, industry, or...
Key tracking software is useful in keeping track of, managing, and improving key control practices. Without organized key tracking, you may be spending more on key control that you need to and you may be unable to address or even notice key security...

Master keys are magic, like having one ring to rule them all. That might be a hyperbolic claim, but a master key is pretty cool. Having a master key system can allow master key holders to carry fewer keys and gain access to multiple areas,...

Small Format Interchangeable Cores, known in the commercial industry as SFIC or more broadly as IC Cores (which can also include large format interchangeable cores or LFIC), are an integral part of most multi-site mechanical key management systems...

Finding a key provider for your organization — whether you are dealing with an outdated, expensive key system or starting fresh with new construction — can be overwhelming. You have to decide who to trust with your organization’s security and who...

In the last couple of decades, the Retail LP/AP industry has evolved from being focused on only catching shoplifters, with limited impact, to being critical to business profitability with as much innovation and sophistication as any other business...

Loss prevention is an important part of every retail business’s bottom line. Your success in preventing loss affects your company, employees, products, and customers. Creating a comprehensive security plan for your organization can feel like a big...

A lock rekey kit is exactly what you might imagine. It is a kit that can be used to change the locks in an organization, without having to call a locksmith. There are no tools required, no hardware removal, and you do not have to have the expertise...

