Comparing the Giants: Key Security Systems Showdown
 Security and accountability have never been more critical for organizations than they are today. Effective management of your company's key security system is critical. It is essential to have a robust system in place that not only ensures the security and accessibility of keys but also allows for seamless tracking and management. This article delves into the different aspects and options for key security systems, offering insights into manual systems, BEST's Keystone Web, and InstaKey’s SecurityRecords.com. Understanding the distinctions, benefits, and limitations of each will aid in making an informed decision for your organization's key security needs.
Security and accountability have never been more critical for organizations than they are today. Effective management of your company's key security system is critical. It is essential to have a robust system in place that not only ensures the security and accessibility of keys but also allows for seamless tracking and management. This article delves into the different aspects and options for key security systems, offering insights into manual systems, BEST's Keystone Web, and InstaKey’s SecurityRecords.com. Understanding the distinctions, benefits, and limitations of each will aid in making an informed decision for your organization's key security needs.
Why Are Key Security Systems Important?
Key tracking is paramount for bolstering an organization's physical security system. Without a dedicated tracking system, organizations risk security breaches and inefficient key control management. Key tracking enforces employee adherence to key usage policies, aids in efficient rekeying processes, and provides crucial data for auditing and evaluating the effectiveness of physical security measures. As organizations expand, the need for a robust key tracking solution becomes indispensable for managing the increasing complexity and volume of key-
related information.
Top Features and Limitations of Manual Key Security Systems
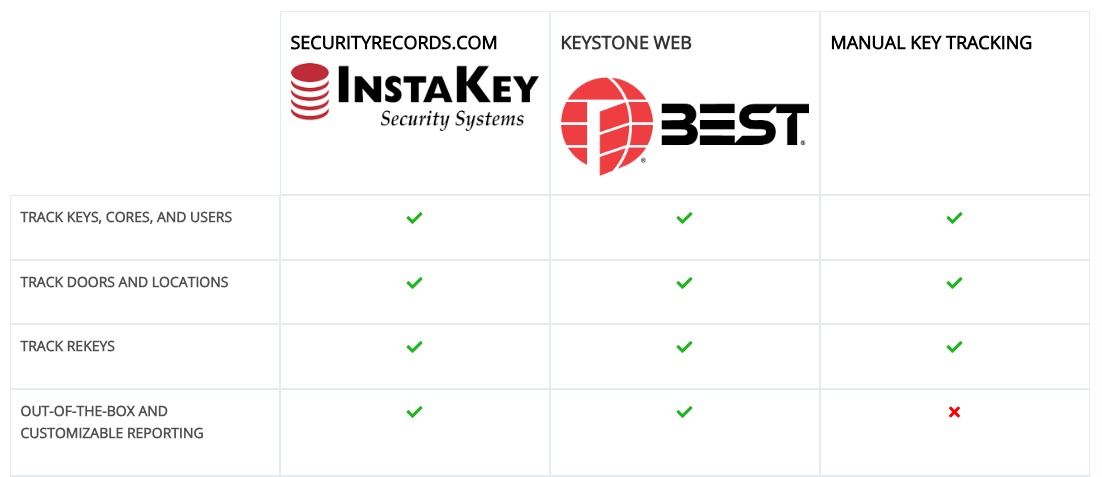
Manual key security systems represent the most basic form of key tracking. If an organization isn’t using dedicated key security systems like InstaKey or BEST, then they are tracking and managing their keys manually. This usually involves managing spreadsheets and paper files.
This approach is the simplest and least expensive option, since there’s no need to invest in dedicated software. It may be ideal for small organizations with one location and a few employees. But it doesn’t scale well, and it becomes less cost-effective as organizations grow in size and complexity.
Top Features of Manual Key Security Systems
● Lowest Initial Cost: There's little to no initial financial investment required, making it budget-friendly.
● Lowest Barrier To Entry: They’re straightforward to implement, especially for smaller organizations.
Limitations of Manual Key Security Systems
● Labor Intensive: Manual key tracking requires a lot of manual data entry and maintenance.
● Lack of Efficiency: The absence of advanced tracking and analytical tools limits the efficiency and accuracy of managing key systems.
● Not Cost-Effective For Larger Organizations: It's not scalable for larger, multifaceted organizations, leading to potential management issues as the organization grows.
● Can Get Complicated: There is difficulty in efficiently managing extensive key data and multiple facilities, potentially leading to security lapses and organizational inefficiencies.
While providing a basic framework for key tracking, manual key security systems just can’t reasonably meet the expanded needs of larger enterprises, especially if they need a way to track their master key system. Those organizations need dedicated key tracking software platforms like the ones we will cover next.
Top Features and Limitations of BEST’s Keystone Web
BEST's Keystone Web emerges as a web-based application aimed at simplifying the key tracking process. Although it has a friendly interface and includes MasterKey Logic for tracking your master key system, it carries certain limitations.
Top Features of BEST’s Keystone Web
● User Friendly: The simple-to-use, browser-based application ensures ease of use and accessibility.
● Specialized Software: The MasterKey Logic is specially designed to meticulously track your master key system, ensuring comprehensive management.
● Customizable Dashboard: Keystone Web offers a customizable dashboard, allowing
users to prioritize and easily access essential information.
Limitations of BEST’s Keystone Web
● Not Optimized For Advanced Lock Systems: The system has restricted functionality for tracking recore changes (or core swaps), potentially leading to management inefficiencies and inaccuracies.
● No Remote Access: Being an intranet application, Keystone Web does not allow for seamless access outside a user’s network, limiting remote management capabilities.
● Key Tracking Challenges: There is no support for digital key receipt collection and cost tracking, leading to potential administrative challenges.
● Requires Manual Action: Site surveys require lock expertise and time, adding to the operational workload.
Keystone Web, while providing a fundamental structure for key management, is more suited for organizations already employing BEST products and requiring basic key tracking capabilities.
Top Features and Limitations of InstaKey's SecurityRecords.com
InstaKey’s SecurityRecords.com stands as a pioneering, cloud-based key tracking software, granting extensive administrative control and a plethora of features for effective and global key management.
Top Features of InstaKey's SecurityRecords.com
● Global Accessibility: SecurityRecords.com allows multiple administrators worldwide to maintain precise and up-to-date records across various locations, ensuring consistent and coordinated key management.
● Comprehensive Capabilities: The platform provides comprehensive tracking, searching, and reporting capabilities across keys, cores, doors, users, and locations, allowing for robust oversight and control.
● Seamless Order Tracking: Users can effortlessly track orders directly from the key tracking dashboard, enhancing operational efficiency.
● Master Key System Management: Efficient management and tracking of master key systems are assured, contributing to enhanced security and organization.
● Broad Compatibility: SecurityRecords.com is compatible with any brand of keying system, with InstaKey adeptly handling chart conversions, ensuring seamless integration and functionality.
Limitations of InstaKey's SecurityRecords.com
● Potential Oversize for Small Organizations: SecurityRecords.com might be an expansive system for smaller organizations with a single location and minimal security requirements, potentially leading to underutilization of the platform’s extensive features.
How Do You Choose A Key Security System?
The choice of key tracking software plays a critical role in enhancing an organization's security and operational efficiency. Before you choose, make sure you start by evaluating your lock and key program. Assess the specific needs of your organization, considering factors like the volume of key data, the number of facilities, and the complexity of the key systems in use. A tailored, robust key tracking system like InstaKey's SecurityRecords.com can significantly bolster your organization's key management, ensuring heightened security and streamlined operations.
Ready to dive deeper into the world of key security systems? Don't miss our detailed side-by-side comparison between InstaKey's SecurityRecords.com, BEST's Keystone Web, and traditional manual key tracking. View the full comparison and make an informed decision for your organization's security needs.