The LP Role of Key Management Systems for a Multi-Site Organization
Loss prevention is an important part of every retail business’s bottom line. Your success in preventing loss affects your company, employees, products, and customers. Creating a comprehensive security plan for your organization can feel like a big undertaking. There are many components that factor into your security plan and loss prevention. As key people, we’re focused on your physical security and how that ties in with your loss prevention efforts. When managing multiple locations within your business, your building security is especially important.
Loss Prevention & Multi-Site Organizations
Every organization with physical products has to worry about loss prevention. Loss prevention can occur on an individual level (internal theft or shoplifting) or on a larger scale (organized retail crime). For multi-site organizations, loss prevention is more challenging as you manage products and people across a number of facilities. Keeping many facilities safe, particularly when you have employees, products, or transportation that happens between locations, takes a strong security plan.
There are many different strategies that businesses can use for loss prevention, but one of the foundational measures to securing your first line of defense is key management. How well you manage your key security and what locks and keys you’re using can be the difference between starting from a secure foundation or building a loss prevention strategy on shaky ground.
All Key Management Systems Are Not Equal
Key management systems are made up of a huge variety of key, lock, and key tracking options. The products you use to build your key management system determine how strong your organization is against unauthorized access. While there are loss prevention practices to put into place regarding employee policies or inventory management, your building security starts with locks and keys. So, what do you need from your key management system to support and secure your multi-site organization?
Restricted Keyways
Duplicate keys can be a serious security risk when managing multiple facilities. With restricted keys, you never have to worry about employees or thieves creating key duplications. Restricted key blanks are not available on the open market, which means that only the manufacturer or licensed entity can provide additional keys, when authorized. When managing multiple facilities, having restricted keys means having assurance that the keys you issue are the only keys in circulation.
User-Rekeyable Cores

Changing or rekeying locks is an unavoidable part of key management. The easier it is for your organization to change the locks in the event of a lost key or other security threat, the easier it is to keep your facilities, employees, and products safe. There are many different locks available on the market, but the most easily managed locks are interchangeable cores.
With interchangeable cores, you don’t need to wait for a locksmith’s help to address a security breach and can replace the lock yourself. To strengthen your key management system further, look for interchangeable cores that are rekeyable. User-rekeyable interchangeable cores allow you to change the locks without a locksmith and without needing to remove hardware from the door. A Step Change key can be used to recombinate a lock, and the keys associated with that modification will be on-hand and ready to be issued. This can be done up to nine times before a key core needs to be replaced. Streamlining your lock changes boosts your overall security while also saving you time and money.
Key Tracking Software
Once you have your keys and locks installed, it’s time to start tracking them. The key tracking world is vast, and tracking methods range from an excel spreadsheet to powerful cloud-based software. For organizations managing multiple sites, the more tracking ability you have, the better your security will be. Here’s what to look for when considering key tracking software options.
Easy to Use
Keeping track of keys and key users isn’t the most exciting day-to-day task. How easy your key tracking software is to use can make a huge difference in your key management and daily responsibilities. Time spent tracking down key information across unwieldy spreadsheets or clunky stand-alone software costs you time and can negatively impact your site security. Software that includes no-contact audit capabilities would be the best opportunity for efficiency. Look for software that takes the difficulty out of key management and is easy to implement and use.
Real-Time Information
When managing keys and access across multiple facilities, having up-to-date information is crucial in maintaining your security and preventing avoidable losses. Managing multiple facilities requires you or your key manager to have real-time updates on who has what keys and what locks those keys have access to. When juggling multiple facilities, you also may have multiple managers who need access to your key tracking software. Your software should support multiple authorized users and allow for real-time information to be securely accessed. Not only should up-to-date info on keys and key assignments be accessible, but key holder records should be effortlessly updated through an integration that updates human resources data regularly.
Easy Updates
With multiple sites comes many employees and access points. Your key tracking software should make it easy to update your records when an employee leaves your organization and returns a key and when a key is transferred to a different key holder. For larger organizations with multiple locations, updates happen frequently, and you need software that can support you at every step. Key tracking software should offer no-contact methods of assigning keys and collecting key receipts, along with the ability to schedule audits to bring locations back to compliance.
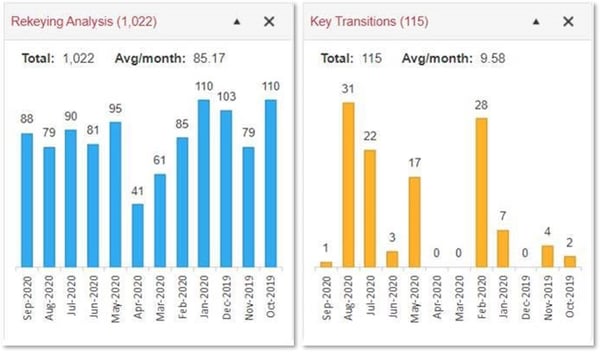
COST Management
Restricted keys and user rekeyable locks are quite effective for reducing spending on locks and keys, but only if managers follow best practices to keep costs down. Key tracking software should also include tools that make it easy to oversee spending on a key system and highlight training opportunities in order to achieve further cost reductions. Are there more rekeys than key transitions? It’s time to check in with managers and train them to get keys back upon employee departures. Are managers rekeying locations even when restricted keys are returned by departing employees? This is an unnecessary expense. It’s time for training.
Comprehensive SOFTWARE AS A SERVICE With InstaKey
InstaKey is known for innovative hardware, but we are a leader in providing key control because our efficient key tracking software and the partnership that supports our clients. We will support your multi-site organization with timely records updates, install coordination, and consultation on best practices to manage your key system. And you can access and track it all in our cloud-based key tracking software — from tracking keys for a single user to an overview of the performance of your entire key system.
Get started on advancing your key management system with SecurityRecords.com®.