Hidden Costs of Traditional IC Core Swaps
When a lock is compromised in your personal life, it’s an easy enough process to replace it or rekey it, whether via a locksmith or by yourself. It’s a relatively cheap one-off expense, a minor inconvenience that arises so rarely, you hardly give it a second thought.
But, if you work as a facilities or loss prevention manager, and it’s your job to ensure the security of your organization’s physical assets, key control is of the utmost concern. And every day, the need for superior security gains new urgency.
When your facilities’ key control is called into question — either by missing keys or, worse, illicit duplicate keys — most of your options to address it are neither cheap nor convenient.
We’ve written before about the benefits of eliminating locksmith callouts. But, what if you manage an IC core swap program instead of relying on a locksmith? You might consider this the next best option. You have more control over when and where cores get swaped out and they keep your facilities secure while saving your organization money -- right?

There’s more to the story. As we explain in this blog post, IC core swap programs have more than a few downsides of their own. There are hidden costs that may cause you to think twice before spending time and budget on cores to swap.
TRACKING DOWN IC CORE SWAP MATERIALS
Maybe you send your cores back and forth from a central location to have them repinned, maybe you continuously order new cores from a supplier. Maybe you repin them in-house for the next go-round. Regardless of how an IC core swap program is managed, you’ll want to keep enough repinned cores stored on-hand for an immediate swap out when the need arises.
Unfortunately, you don’t have as much control over materials as you wish you did. Managing a core swap program effectively requires a significant amount of organization, attention to detail and a supplier partner that can get you the materials you need, when you need them. Tracking and managing all of these materials can easily become a full-time job for one person, depending on the number of locations supported. The most frustrating issues often arise in the reliance on your supplier. Slow order turnarounds and issues with order accuracy can make a key control program ineffective and less than secure, very quickly and you’ll end up dedicating more time and effort to managing this program, which can be more costly than you bargained for. Sure, the cores are cheap, but your savings are immediately eliminated when you lose one or more team members to managing core swaps.
IC CORE SWAP PROGRAM SECURITY
If you’re left waiting on materials from your supplier, there may be gaps between when a core swap is needed and when it’s actually completed, leaving your facilities vulnerable to a security breach. Not only is timing an issue, but the key system itself may be less secure than you think. IC cores are generally accepted as standard security in a commercial first line of defense. But, consider for a moment the keys. Sure, the cores are secure, but what happens when a key holder can take a key to be duplicated whenever they want?
Maybe the keys in your key system are stamped DO NOT DUPLICATE. That means keys can’t or won’t be duplicated, right? That assumption is incorrect. That stamp is just a request. These keys can be copied by any willing locksmith, hardware store employee or automated key duplication machine. There are keys that truly cannot be copied, however. Those are restricted keys. These key blanks are tightly controlled by their manufacturer and cannot be found on the open market. If a key blank is not available, a copy cannot be made. Unfortunately, most SFIC systems don’t utilize these keys, which can be another hidden cost in the form of a potential security breach. Additionally, if keys are not restricted, a core swap will be needed each time a key holder departs from the organization, whether or not you get their keys back upon their departure. This is because you can’t be sure that a duplicate key hasn’t been made and stored away for nefarious use later. This causes additional spending on securing a key system.
Surely there is a more efficient, cost-effective method to secure facilities with IC cores, right?
THE INSTAKEY ADVANTAGE
As it turns out, there is a more efficient, cost-effective method of key control for multi-site facilities.
InstaKey offers the same end result of a traditional IC core swap program, with none of the added time, costs or risks. In fact, cores only need to be swapped out once for every nine times you would swap out other IC cores. That’s because these cores can be rekeyed, without removing them, up to nine times.
Our user-rekeyable locks are ingeniously designed around one simple action: The 180-degree turn of a Step Change Key. That’s it. The old user keys are obsolete, and new keys will be on-hand to assign to key holders. All of the materials needed to restore facility security will be on- hand and ready for immediate use. No more waiting on suppliers to fulfill orders. Security can be restored immediately. Once a Rekeying Kit is used, just order the next one and be prepared ahead of time.
With traditional IC core swaps, you have to worry about time and accuracy. With InstaKey, rekeying the lock is quick, simple and reliable. On top of that, the time required to manage this program is minimal, allowing your team to stay focused on other important programs and initiatives. Rekeying Kits are packaged and labeled to keep materials organized and coordinated, allowing personnel to easily address the affected locks in a fraction of the time.
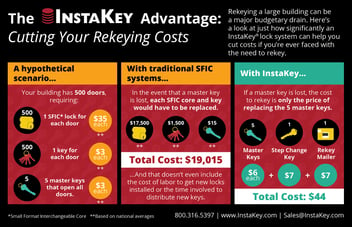
As for cost: up-front costs to implement the system are a little higher than traditional IC cores, but that will include a Rekeying Kit for the first rekey. Each rekey after that is essentially equivalent to the cost to replace keys. A basic setup with an average of 5 keys per location will cost between $30-$40 to rekey all of the locks in location, compared to $30-$40 per core when you’re managing a traditional core swap program.
When it comes to the security risks inherent in a non-restricted key systems, an InstaKey KeyControl® Program comes complete with restricted keys to enhance security. You cannot get InstaKey keys copied, but we’ll happily provide additional keys as needed, upon authorization. Our keys are also serialized to make it easy to track serial numbered keys to key holders.
With InstaKey, you can eliminate the risky, time-consuming, expensive process of managing a core swap program. Instead of worrying about whether or not you’ll be able to quickly and effectively secure your facility, you can relax with the knowledge that you have a key control system that is affordable, reliable and easy to manage.